- Australia
- Bahrain
- Belgien
- Belgique
- België
- Canada
- Canada (Français)
- Danmark
- Deutschland
- Eesti
- España
- Estonia - English
- France
- Hong Kong
- Iceland
- India
- Ireland
- Israel
- Italia
- Jordan
- Kuwait
- Latvija
- Lebanon
- Lietuva
- Luxembourg
- Magyarország
- Malta
- Nederland
- New Zealand
- Norge
- Oman
- Polska
- Portugal
- Qatar
- Saudi Arabia
- Schweiz
- Slovenia
- Slovenská Republika
- South Africa
- Suisse
- Suomi
- Sverige
- Svizzera
- Türkiye
- United Arab Emirates
- United Kingdom
- United States
- Österreich
- Česká Republika
- България
- ישראל
- إسرائيل
- الأردن
- الإمارات العربية المتحدة
- البحرين
- الكويت
- المملكة العربية السعودية
- دولة قطر
- سلطنة عمان
- لبنان
- 日本
- 대한민국
-
Learn About CGM
-
What is CGM?
What is CGM?
Continuous Glucose Monitoring (CGM) is a method to track glucose levels throughout the day and night.
Learn More
-
CGM vs. BGM
CGM vs. BGM
Blood Glucose Meters (BGM) measure glucose levels at a single moment in time, while Continuous Glucose Monitoring (CGM) systems continually check glucose levels throughout the day and night.
Learn More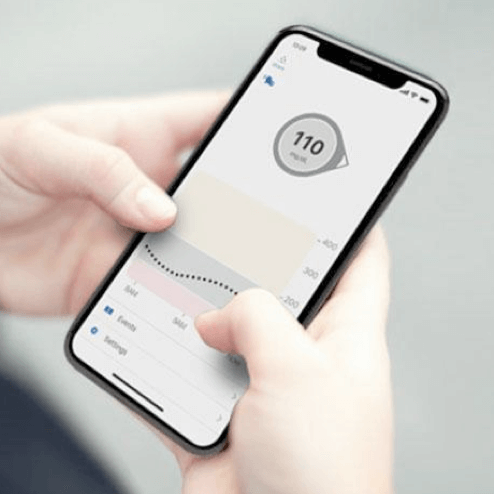
-
Benefits of CGM
MM: Benefits of CGM
Benefits of CGM
Unlike a blood glucose meter (BGM), which provides just a single glucose reading. CGM systems can provide real-time, dynamic glucose information every five minutes.
Learn More
- CGM FAQs
-
What is CGM?
-
Products
-
Dexcom G6 CGM System
- Dexcom G6 CGM System
- Dexcom G6 Overview
- How it Works
- Features & Benefits
- Integrations & Compatibility

-
Dexcom G6 CGM System for Medicare
- Dexcom G6 CGM System for Medicare
- Dexcom G6 Overview
- Integrations & Compatibility
- Medicare Product Support

-
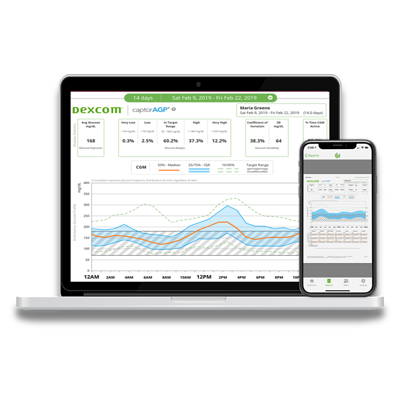
Software & Mobile Apps
- Software & Mobile Apps
- Dexcom CLARITY Reporting Software
- Dexcom Mobile & Watch Apps
- Follow App for Friends & Family
- Product FAQs
-
Dexcom G6 CGM System
-
Warrior Community
-
Customer Stories
Customer Stories
At Dexcom, our customers are our heroes - read our Warrior stories to learn more.
Read Customer Stories Read Celebrity & Influencer Stories
-
Become a Dexcom Warrior
Become a Dexcom Warrior
Apply today and share your story with us by providing some information about yourself and your experience with Dexcom.
Apply Today
-
Advocacy Organizations
Advocacy Organizations
Looking for helpful diabetes resources? Review our list of contact information for national organizations committed to helping those with diabetes, and their families, find support and guidance.
Learn More
-
Customer Stories
-
Support
